Why Bitcoin Wallets Need Block Filters
With the advent of software development kits like BDK and LDK, building a bitcoin wallet has never been easier. However, as much ease of development is necessary, it is important that it is built in a way that protects users’ security and privacy by default. For example, how a lightweight wallet connects to a third-party server to receive and send transaction data is an important issue to address.
I believe bitcoin wallets need block filters to respect a user’s privacy. Why; It is the only way to prevent the server from leaking data, which would allow it to link a user’s transaction data beyond what is publicly available.
In this article, we’ll explore why bitcoin wallets need block filters by first looking at how many bitcoin users are running full nodes, how API wallets offer a good user experience but ultimately lead to all your transactions being linked together, how bloom filters failed to protect privacy, how block filters are the only lightweight wallet network privacy solution, and finally how all of this can be implemented using Tor-only communication to protect a user’s IP address.
Only a few users run full nodes
Running and using a Bitcoin node is the best thing you can do because you are part of the network and don’t need intermediaries to receive and transmit transaction data. However, it’s clear that running a full hub isn’t for everyone. the existence and need for light clients (Simple Payment Verification) was even envisioned by Satoshi at Bitcoin White Paper.
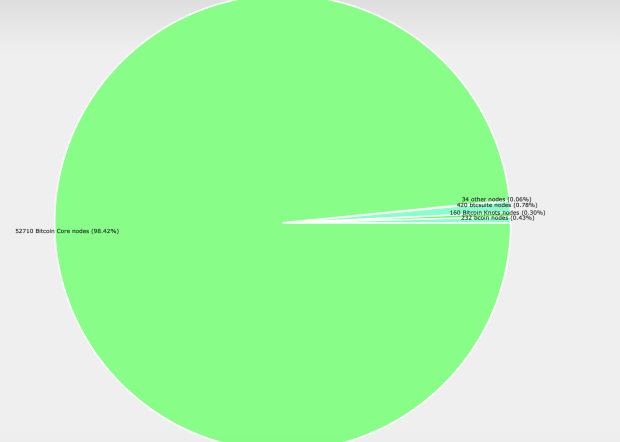
We cannot know how many users are running a full node, we can only know how many nodes exist. Conservative estimates counting only listening nodes would put this number at about 16,000, as shown in Bitnodes.io web page. More accurate estimates that measure both listening and non-listening nodes, such as Node counter tool by Luke Dashjr pushed that number higher, to about 53,000.
It is also important to know the historical context of the number of bitcoin full nodes. According to Bitcoin Node Count History by Luke Dashjr, we can observe that the use of bitcoin nodes is far from its peak. On January 13, 2018 the count reached 205,000. This had a lot to do with the fact that bitcoin had hit a previous all-time high a few weeks earlier. In 2021, we can notice that the number of nodes also increased when the price went up, but only reached close to 90,000.
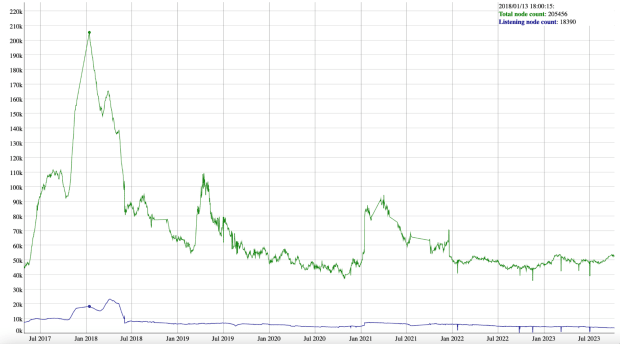
We can confirm that there are few users running bitcoin nodes and that this number is not increasing over time. Lightweight wallets are much easier to use than a bitcoin node and we need to find the right network privacy solution to implement. Let’s take a look at the most used technology today, which is API wallets.
API wallet service providers collect your data by default
Most bitcoin wallets use an API (Application Specific Interface) to send and receive user transaction data. This technology is highly scalable and provides the best user experience as requests are instantaneous. However, it has an inherent privacy warning. Let’s break down how it works and how service providers collect your data by default.
When you initialize a standard bitcoin wallet, you enter or generate a mnemonic and set the desired generation path (often automatically). This gives you a master public key, often called xpub. Here’s how it looks:
xpub6CUGRUonZSQ4TWtTMmzXdrXDtypWKiKrhko4egpiMZbpiaQL2jkwSB1icqYh2cfDfVxdx4df189oLKnC5fSwqPfgyP3hooxujYzAu3fDVmz
Once this is done, xpub is automatically sent to the service provider’s server, where it pulls bitcoin addresses within the gap limit (how many unused addresses with zero balance will be checked before the server stops scanning for money). These addresses are searched in the server’s index and if transactions are found, they are sent to the user’s client. Addresses are monitored in case new transactions occur. Furthermore, when a user sends a transaction, it is also sent through the same communication channel.
It is obvious that this process is very efficient and allows API wallets to provide a fast and easy user experience. However, the service provider will be able to link all our transactions together and thus collect your personal information by default. Fortunately, many API wallets allow users to connect via Tor, so at least a user’s IP address is protected.
Let us now consider an alternative method that does not depend on a single server, the use of bloom filters in lightweight wallets.
Why Bloom Filters Don’t Work for Privacy
Some wallets allow a user to receive and send transaction data through Bloom filters. This method of communication was introduced in BIP37 and was originally thought to be private. In this section, we’ll break down what Bloom filters are and why they’re actually bad for privacy.
Bloom filters are probabilistic data structures used to test whether an item is a member of a set. In the bitcoin context, bloom filters are created by a light client and sent to network peers, who check whether there is a match between an address (item) and the blockchain data (set). If there is a match, the transaction data is sent to the light client. It is probabilistic because there are false positives, but these are later discarded by the light client.
It was assumed that the false positive rate would be high enough that a network peer would not be able to tell which transactions were really yours and which were fake. However, due to an implementation error, the false positive rate actually decreased.
Additionally, a light client can create different bloom filters for the same wallet, and if two or more are collected from a network peer, the intersection can be calculated to remove false positives. Finally, if the blockchain data is analyzed and the user does not coinjoin or use coin control, a network peer can deduce which addresses do not belong to the user.
You can read more about privacy issues with BIP37 here. Now let’s look at the rest of the light client network solution.
A Bitcoin wallet needs blocking filters to protect privacy
Back in 2018, there was no real solution to this problem, block filters weren’t a thing yet. Fortunately, they were introduced the following year BIP157 and 158and are now implemented in several bitcoin wallets and software such as Wasabi, Blixt, Breez, LNDand LDK. They are often referred to as neutrinos. In this section, we’ll look at how they work and why they’re the right solution for network privacy.
Block filters compress block data to help wallets receive transactions from peers without compromising privacy by downloading specific blocks instead of looking for individual transactions.
The block filter process typically involves three steps. First, a user downloads the block filters representing the blockchain from a peer network in the case of Breez, or from the moderator server in the case of Wasabi. The light client then checks if the addresses within the gap limit match a block filter. Finally, if there is a match, the corresponding block is downloaded.
Because we download entire blocks instead of individual transactions, and because there is a false positive rate, the blocking filter method works to protect a user’s privacy from network peers. Unlike Bloom filters and API wallets, it cannot understand (or directly collect) the connection between a user’s transactions, other than what is publicly known on the blockchain.
Block filters are part of the network privacy solution, but something else is needed to complete the picture.
Tor is the last piece left to solve network privacy
Tor and bitcoin go hand in hand and together with block filters, can solve network privacy for light clients. Tor hides a user’s IP address from the destination server by routing it through a network of nodes. This mechanism is called onion routing because of the multiple layers of communication.
Tor filtering and blocking have one thing in common. They are both processes that can slow down performance and that can be noticeable and degrade the user experience. Some people think you just have to accept it, but I think it can be improved to the point where it’s barely noticeable.
For example, the Tor community has implemented a communication reliability solution called Confluence. Instead of making a single request, clients make two requests using two different Tor circuits to increase the likelihood of fast completion. This, along with innovations in wallet loading for block filters such as Turbosync in the Wasabi wallet, it will lead us to a future where the user does not have to choose between usability and privacy, but can enjoy both.
This is a guest post byGustavo Flores Echaiz. The views expressed are entirely their own and do not necessarily reflect those of BTC Inc or Bitcoin Magazine.





