Light Clients and Proof of Stake

Particular due to Vlad Zamfir and Jae Kwon for a lot of of the concepts described on this submit
Other than the first debate round weak subjectivity, one of the necessary secondary arguments raised towards proof of stake is the problem that proof of stake algorithms are a lot more durable to make light-client pleasant. Whereas proof of work algorithms contain the manufacturing of block headers which will be rapidly verified, permitting a comparatively small chain of headers to behave as an implicit proof that the community considers a specific historical past to be legitimate, proof of stake is more durable to suit into such a mannequin. As a result of the validity of a block in proof of stake depends on stakeholder signatures, the validity is determined by the possession distribution of the forex within the specific block that was signed, and so it appears, at the very least at first look, that so as to achieve any assurances in any respect concerning the validity of a block, the complete block should be verified.
Given the sheer significance of mild consumer protocols, significantly in mild of the recent corporate interest in “internet of things” functions (which should usually essentially run on very weak and low-power {hardware}), mild consumer friendliness is a vital characteristic for a consensus algorithm to have, and so an efficient proof of stake system should handle it.
Light shoppers in Proof of Work
Usually, the core motivation behind the “light client” idea is as follows. By themselves, blockchain protocols, with the requirement that each node should course of each transaction so as to guarantee safety, are costly, and as soon as a protocol will get sufficiently common the blockchain turns into so massive that many customers grow to be not even capable of bear that value. The Bitcoin blockchain is at the moment 27 GB in size, and so only a few customers are keen to proceed to run “full nodes” that course of each transaction. On smartphones, and particularly on embedded {hardware}, working a full node is outright not possible.
Therefore, there must be a way through which a consumer with far much less computing energy to nonetheless get a safe assurance about numerous particulars of the blockchain state – what’s the stability/state of a specific account, did a specific transaction course of, did a specific occasion occur, and so on. Ideally, it needs to be doable for a light-weight consumer to do that in logarithmic time – that’s, squaring the quantity of transactions (eg. going from 1000 tx/day to 1000000 tx/day) ought to solely double a light-weight consumer’s value. Thankfully, because it seems, it’s fairly doable to design a cryptocurrency protocol that may be securely evaluated by mild shoppers at this stage of effectivity.
Primary block header mannequin in Ethereum (word that Ethereum has a Merkle tree for transactions and accounts in every block, permitting mild shoppers to simply entry extra information)
In Bitcoin, mild consumer safety works as follows. As a substitute of developing a block as a monolithic object containing all of the transactions straight, a Bitcoin block is cut up up into two components. First, there’s a small piece of information known as the block header, containing three key items of information:
- The hash of the earlier block header
- The Merkle root of the transaction tree (see beneath)
- The proof of work nonce
Further information just like the timestamp can be included within the block header, however this isn’t related right here. Second, there’s the transaction tree. Transactions in a Bitcoin block are saved in a knowledge construction known as a Merkle tree. The nodes on the underside stage of the tree are the transactions, and then going up from there each node is the hash of the 2 nodes beneath it. For instance, if the underside stage had sixteen transactions, then the subsequent stage would have eight nodes: hash(tx[1] + tx[2]), hash(tx[3] + tx[4]), and so on. The extent above that may have 4 nodes (eg. the primary node is the same as hash(hash(tx[1] + tx[2]) + hash(tx[3] + tx[4]))), the extent above has two nodes, and then the extent on the high has one node, the Merkle root of the complete tree.
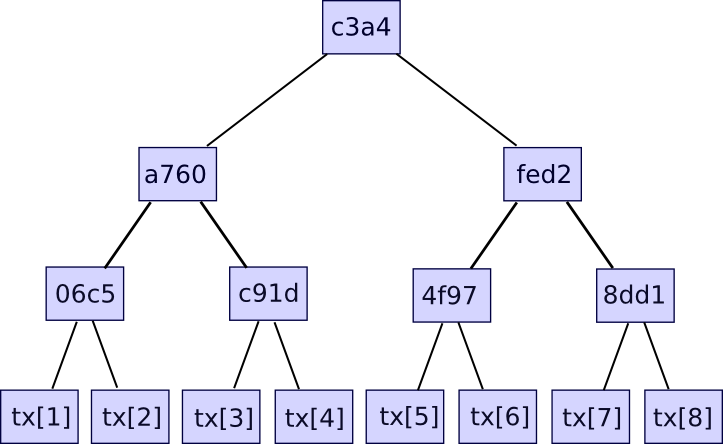
The Merkle root will be thought of as a hash of all of the transactions collectively, and has the identical properties that you’d count on out of a hash – for those who change even one bit in a single transaction, the Merkle root will find yourself fully completely different, and there is no such thing as a strategy to give you two completely different units of transactions which have the identical Merkle root. The explanation why this extra sophisticated tree development must be used is that it truly means that you can give you a compact proof that one specific transaction was included in a specific block. How? Basically, simply present the department of the tree happening to the transaction:
The verifier will confirm solely the hashes happening alongside the department, and thereby be assured that the given transaction is legitimately a member of the tree that produced a specific Merkle root. If an attacker tries to alter any hash anyplace happening the department, the hashes will not match and the proof can be invalid. The dimensions of every proof is the same as the depth of the tree – ie. logarithmic within the quantity of transactions. In case your block incorporates 220 (ie. ~1 million) transactions, then the Merkle tree could have solely 20 ranges, and so the verifier will solely have to compute 20 hashes so as to confirm a proof. In case your block incorporates 230 (ie. ~1 billion) transactions, then the Merkle tree could have 30 ranges, and so a light-weight consumer will be capable of confirm a transaction with simply 30 hashes.
Ethereum extends this fundamental mechanism with a two further Merkle timber in every block header, permitting nodes to show not simply {that a} specific transaction occurred, but additionally {that a} specific account has a specific stability and state, {that a} specific occasion occurred, and even {that a} specific account does not exist.
Verifying the Roots
Now, this transaction verification course of all assumes one factor: that the Merkle root is trusted. If somebody proves to you {that a} transaction is a component of a Merkle tree that has some root, that by itself means nothing; membership in a Merkle tree solely proves {that a} transaction is legitimate if the Merkle root is itself recognized to be legitimate. Therefore, the opposite essential half of a light-weight consumer protocol is determining precisely the way to validate the Merkle roots – or, extra typically, the way to validate the block headers.
First of all, allow us to decide precisely what we imply by “validating block headers”. Light shoppers should not succesful of totally validating a block by themselves; protocols exist for doing validation collaboratively, however this mechanism is dear, and so so as to forestall attackers from losing everybody’s time by throwing round invalid blocks we’d like a method of first rapidly figuring out whether or not or not a specific block header is most likely legitimate. By “probably valid” what we imply is that this: if an attacker provides us a block that’s decided to be most likely legitimate, however just isn’t truly legitimate, then the attacker must pay a excessive value for doing so. Even when the attacker succeeds in quickly fooling a light-weight consumer or losing its time, the attacker ought to nonetheless undergo greater than the victims of the assault. That is the usual that we are going to apply to proof of work, and proof of stake, equally.
In proof of work, the method is straightforward. The core thought behind proof of work is that there exists a mathematical operate which a block header should fulfill so as to be legitimate, and it’s computationally very intensive to supply such a legitimate header. If a light-weight consumer was offline for some interval of time, and then comes again on-line, then it can search for the longest chain of legitimate block headers, and assume that that chain is the reliable blockchain. The fee of spoofing this mechanism, offering a sequence of block headers that’s probably-valid-but-not-actually-valid, may be very excessive; in actual fact, it’s virtually precisely the identical as the price of launching a 51% assault on the community.
In Bitcoin, this proof of work situation is straightforward: sha256(block_header) < 2**187 (in follow the “target” worth modifications, however as soon as once more we are able to dispense of this in our simplified evaluation). With the intention to fulfill this situation, miners should repeatedly attempt completely different nonce values till they arrive upon one such that the proof of work situation for the block header is glad; on common, this consumes about 269 computational effort per block. The elegant characteristic of Bitcoin-style proof of work is that each block header will be verified by itself, with out counting on any exterior data in any respect. Which means the method of validating the block headers can in actual fact be finished in fixed time – obtain 80 bytes and run a hash of it – even higher than the logarithmic sure that we’ve got established for ourselves. In proof of stake, sadly we shouldn’t have such a pleasant mechanism.
Light Clients in Proof of Stake
If we need to have an efficient mild consumer for proof of stake, ideally we want to obtain the very same complexity-theoretic properties as proof of work, though essentially another way. As soon as a block header is trusted, the method for accessing any information from the header is similar, so we all know that it’s going to take a logarithmic quantity of time so as to do. Nonetheless, we would like the method of validating the block headers themselves to be logarithmic as properly.
To begin off, allow us to describe an older model of Slasher, which was not significantly designed to be explicitly light-client pleasant:
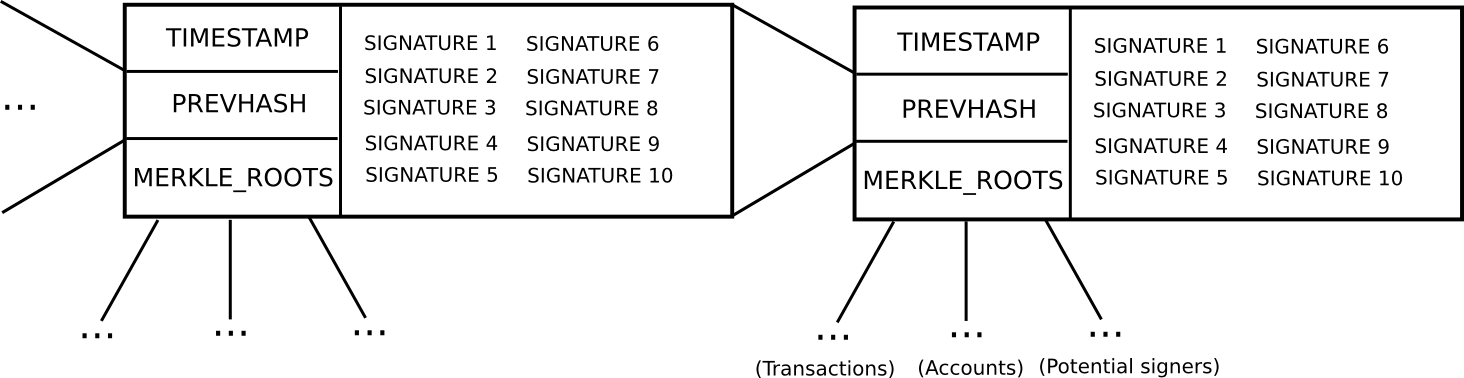
- With the intention to be a “potential blockmaker” or “potential signer”, a consumer should put down a safety deposit of some measurement. This safety deposit will be put down at any time, and lasts for an extended interval of time, say 3 months.
- Throughout each time slot T (eg. T = 3069120 to 3069135 seconds after genesis), some operate produces a random quantity R (there are numerous nuances behind making the random quantity safe, however they don’t seem to be related right here). Then, suppose that the set of potential signers ps (saved in a separate Merkle tree) has measurement N. We take ps[sha3(R) % N] because the blockmaker, and ps[sha3(R + 1) % N], ps[sha3(R + 2) % N] … ps[sha3(R + 15) % N] because the signers (basically, utilizing R as entropy to randomly choose a signer and 15 blockmakers)
- Blocks consist of a header containing (i) the hash of the earlier block, (ii) the checklist of signatures from the blockmaker and signers, and (iii) the Merkle root of the transactions and state, in addition to (iv) auxiliary information just like the timestamp.
- A block produced throughout time slot T is legitimate if that block is signed by the blockmaker and at the very least 10 of the 15 signers.
- If a blockmaker or signer legitimately participates within the blockmaking course of, they get a small signing reward.
- If a blockmaker or signer indicators a block that’s not on the primary chain, then that signature will be submitted into the primary chain as “evidence” that the blockmaker or signer is making an attempt to take part in an assault, and this results in that blockmaker or signer shedding their deposit. The proof submitter could obtain 33% of the deposit as a reward.
In contrast to proof of work, the place the inducement to not mine on a fork of the primary chain is the chance value of not getting the reward on the primary chain, in proof of stake the inducement is that for those who mine on the unsuitable chain you’re going to get explicitly punished for it. That is necessary; as a result of a really great amount of punishment will be meted out per unhealthy signature, a a lot smaller quantity of block headers are required to realize the identical safety margin.
Now, allow us to look at what a light-weight consumer must do. Suppose that the sunshine consumer was final on-line N blocks in the past, and desires to authenticate the state of the present block. What does the sunshine consumer have to do? If a light-weight consumer already is aware of {that a} block B[k] is legitimate, and desires to authenticate the subsequent block B[k+1], the steps are roughly as follows:
- Compute the operate that produces the random worth R throughout block B[k+1] (computable both fixed or logarithmic time relying on implementation)
- Given R, get the general public keys/addresses of the chosen blockmaker and signer from the blockchain’s state tree (logarithmic time)
- Confirm the signatures within the block header towards the general public keys (fixed time)
And that is it. Now, there’s one gotcha. The set of potential signers could find yourself altering in the course of the block, so it appears as if a light-weight consumer may have to course of the transactions within the block earlier than having the ability to compute ps[sha3(R + k) % N]. Nonetheless, we are able to resolve this by merely saying that it is the potential signer set from the beginning of the block, or perhaps a block 100 blocks in the past, that we’re choosing from.
Now, allow us to work out the formal safety assurances that this protocol provides us. Suppose {that a} mild consumer processes a set of blocks, B[1] … B[n], such that each one blocks ranging from B[k + 1] are invalid. Assuming that each one blocks as much as B[k] are legitimate, and that the signer set for block B[i] is decided from block B[i – 100], which means the sunshine consumer will be capable of appropriately deduce the signature validity for blocks B[k + 1] … B[k + 100]. Therefore, if an attacker comes up with a set of invalid blocks that idiot a light-weight consumer, the sunshine consumer can nonetheless make sure that the attacker will nonetheless need to pay ~1100 safety deposits for the primary 100 invalid blocks. For future blocks, the attacker will be capable of get away with signing blocks with faux addresses, however 1100 safety deposits is an assurance sufficient, significantly because the deposits will be variably sized and thus maintain many thousands and thousands of {dollars} of capital altogether.
Thus, even this older model of Slasher is, by our definition, light-client-friendly; we are able to get the identical form of safety assurance as proof of work in logarithmic time.
A Higher Light-Shopper Protocol
Nonetheless, we are able to do considerably higher than the naive algorithm above. The important thing perception that lets us go additional is that of splitting the blockchain up into epochs. Right here, allow us to outline a extra superior model of Slasher, that we are going to name “epoch Slasher”. Epoch Slasher is equivalent to the above Slasher, aside from a couple of different circumstances:
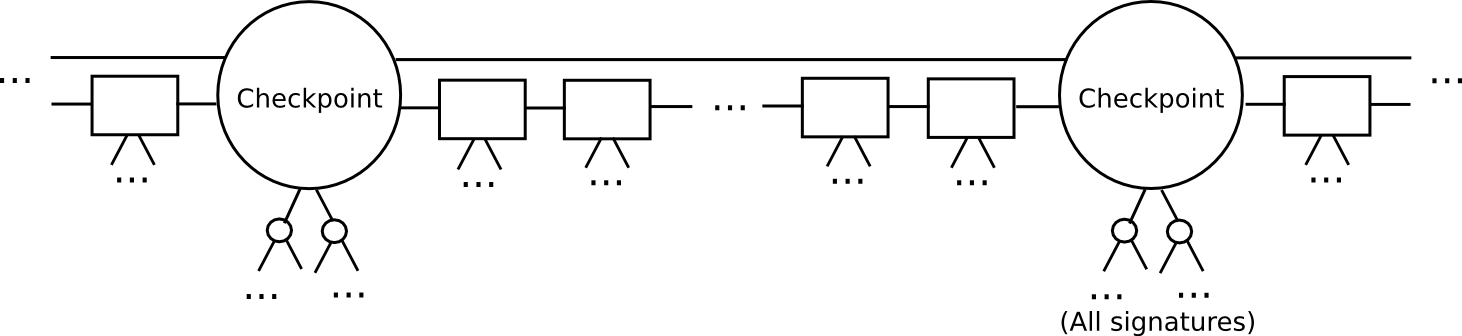
- Outline a checkpoint as a block such that block.quantity % n == 0 (ie. each n blocks there’s a checkpoint). Suppose of n as being someplace round a couple of weeks lengthy; it solely must be considerably lower than the safety deposit size.
- For a checkpoint to be legitimate, 2/3 of all potential signers need to approve it. Additionally, the checkpoint should straight embrace the hash of the earlier checkpoint.
- The set of signers throughout a non-checkpoint block needs to be decided from the set of signers in the course of the second-last checkpoint.
This protocol permits a light-weight consumer to catch up a lot sooner. As a substitute of processing each block, the sunshine consumer would skip on to the subsequent checkpoint, and validate it. The sunshine consumer may even probabilistically verify the signatures, selecting out a random 80 signers and requesting signatures for them particularly. If the signatures are invalid, then we will be statistically sure that 1000’s of safety deposits are going to get destroyed.
After a light-weight consumer has authenticated as much as the newest checkpoint, the sunshine consumer can merely seize the newest block and its 100 mother and father, and use a less complicated per-block protocol to validate them as within the authentic Slasher; if these blocks find yourself being invalid or on the unsuitable chain, then as a result of the sunshine consumer has already authenticated the newest checkpoint, and by the foundations of the protocol it may be positive that the deposits at that checkpoint are lively till at the very least the subsequent checkpoint, as soon as once more the sunshine consumer can make sure that at the very least 1100 deposits can be destroyed.
With this latter protocol, we are able to see that not solely is proof of stake simply as succesful of light-client friendliness as proof of work, however furthermore it is truly much more light-client pleasant. With proof of work, a light-weight consumer synchronizing with the blockchain should obtain and course of each block header within the chain, a course of that’s significantly costly if the blockchain is quick, as is one of our personal design targets. With proof of stake, we are able to merely skip on to the newest block, and validate the final 100 blocks earlier than that to get an assurance that if we’re on the unsuitable chain, at the very least 1100 safety deposits can be destroyed.
Now, there’s nonetheless a reliable position for proof of work in proof of stake. In proof of stake, as we’ve got seen, it takes a logarithmic quantity of effort to probably-validate every particular person block, and so an attacker can nonetheless trigger mild shoppers a logarithmic quantity of annoyance by broadcasting unhealthy blocks. Proof of work alone will be successfully validated in fixed time, and with out fetching any information from the community. Therefore, it could make sense for a proof of stake algorithm to nonetheless require a small quantity of proof of work on every block, making certain that an attacker should spend some computational effort so as to even barely inconvenience mild shoppers. Nonetheless, the quantity of computational effort required to compute these proofs of work will solely should be miniscule.





